
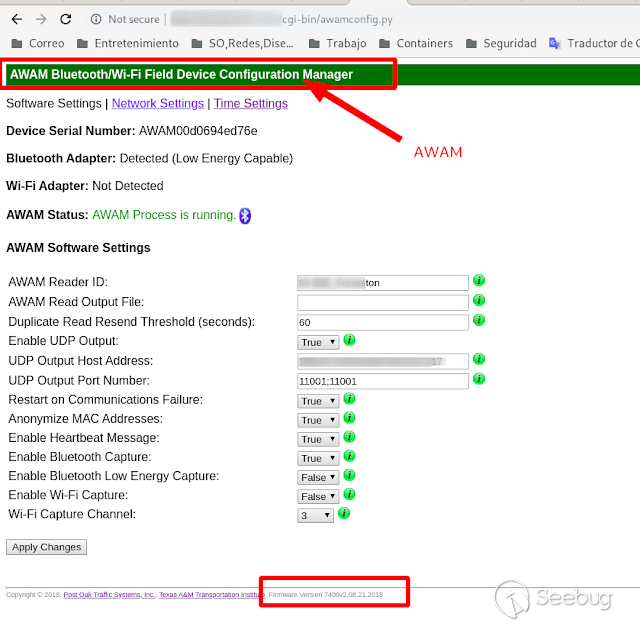
"AWAM Bluetooth Field Device" devices, as the company behind them "http://www.postoaktraffic.com/" says, are devices for monitoring traffic, by capturing the MAC addresses of the Bluetooth devices that you could commonly have in your car, such as cell phone, headphones or the car's own bluetooth. This simply seemed very interesting, so I decided to test the safety of these devices.
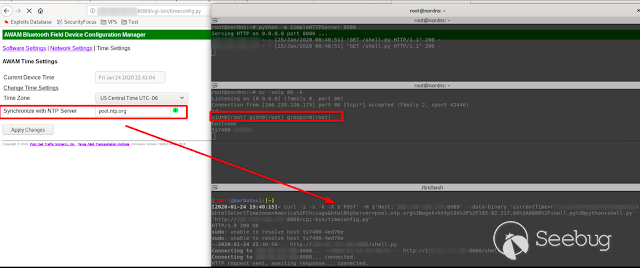
As I recently got an injection of code in a device with similar characteristics I decided to try the same route
So, in the "Time Settings" function it is possible to inject commands, just by casting ";" after the hostname of the NTP server to which you want to synchronize. So using "Curl" I assemble the following command to achieve a reverse shell
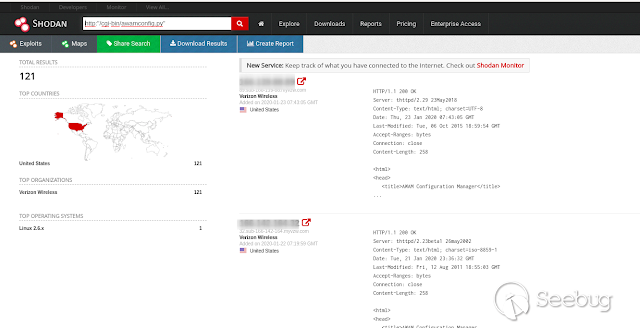
Shodan:
Affected versions:
Firmware Version 7400v2.08.21.2018
Firmware Version 7800SD.2015.1.16
Firmware Version 2011.3
Firmware Version 7400v2.02.01.2019
Firmware Version 7800SD.2012.12.5


暂无评论