### Authenticated RCE on Comtech FX Series (CVE-2020-5179)
The web application used for the management and administration of Compression
Bandwidth Optimization Platform has a critical vulnerability that allow to an
attacker to do a Remote Code Execution with root access. That is, the
application allows to gain full control over the server.
[](https://images.seebug.org/1583428040774-w331s)
_Comtech logo._
#### Comtech Stampede FX-1010
_[](https://images.seebug.org/1583428043611-w331s)_
Vendor WebSite:
<http://www.comtechtel.com/>
You can search for vulnerable sites on google with the following dork **"
Comtech FX Series"** or maybe in shodan if you want.
**Let 's start!!**
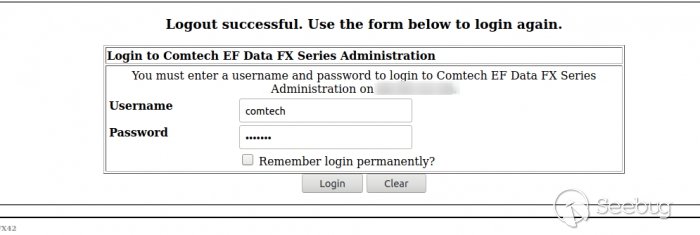
We need to use the default comtech credentials to access on the administration
panel (comtech:comtech)
[](https://images.seebug.org/1583428052566-w331s)
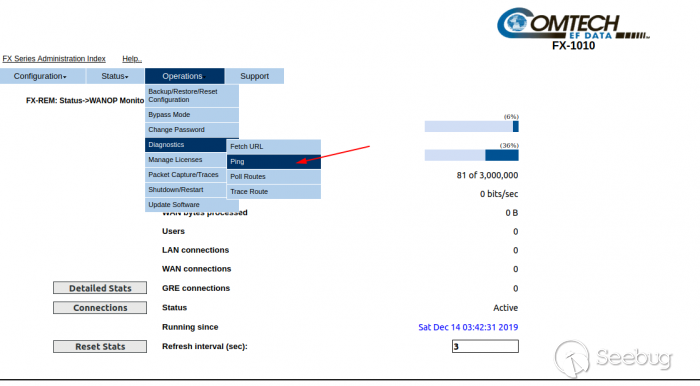
Go to the Menu and click on Operations > Diagnostics > Ping
[
](https://images.seebug.org/1583428057846-w331s)
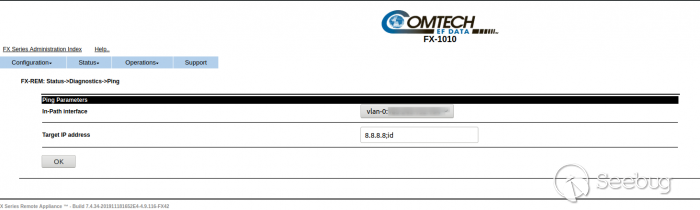
On target IP Address input we can ping an IP but we can add other command
behind of ";" in this case, we are going to use an "id" command.
[](https://images.seebug.org/1583428060906-w331s)
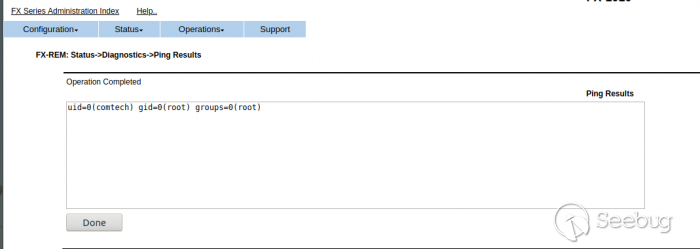
When we press OK, the result show us the user and groups.
[](https://images.seebug.org/1583428079108-w331s)
It's time to automate!
Thanks to [SamneZ](https://twitter.com/s4mnez) for help me with the script on
Python


暂无评论